Business operation challenges
Along with the development of each business are the challenges arising in the process of corporate governance in general, the management of identity and access to the information assets system in particular. Challenges in identifying and managing access and accounts of the system are as follows:
- Companies, enterprises often own a system consists of many IT applications. Over time, along with the changing needs of business, the system will grow in size and in the number of applications.
- Each application has a separate set of user accounts. The number of user accounts across the system grows exponentially as the number of applications grows. Managing accounts by hierarchy and function will be complex, error-prone and out-of-control, contain many security risks.
- Management of account and access of the system is an important task, requiring compliance with the business policies to ensure the security, availability, integrity of system information.
- Operational policies within the business still have weaknesses or unplanned problems. It is difficult to have a perfect and complete policy.
- Especially for financial and banking institutions, the management of account identity is extremely important, affecting closely business and operation.
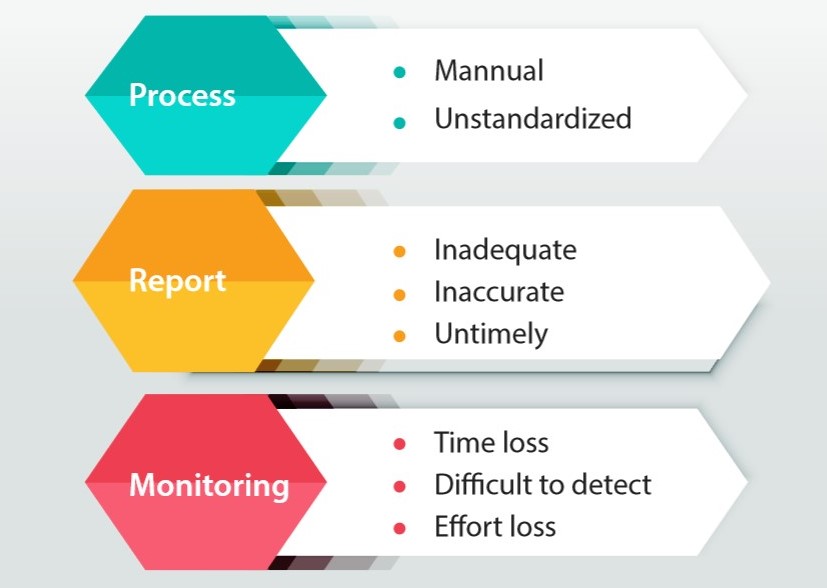
Risks of business operationWith the traditional management approach, using human resources to solve the identity management problem, enterprises will face risks such as:
- From the manager's point of view: Cannot put absolute trust in the accuracy of the report, often have to consider, enhance process improvement.
- From the system administrator's point of view: The tasks must be numerous, complex and error-prone. Periodic inspections bring tremendous pressure, both in terms of progress and accuracy.
Identity & Access management (IAM) solution
IAM offers a strong management system so enterprises can do:
- Solve challenges of identity management
- Systemize the process of managing the account life cycle of each individual
- Computerize, automate access authorization processes
- Integrate with other application systems, allowing user to allocate / revoke user accounts of each system
- Report for auditing and monitoring of user access across enterprise application system
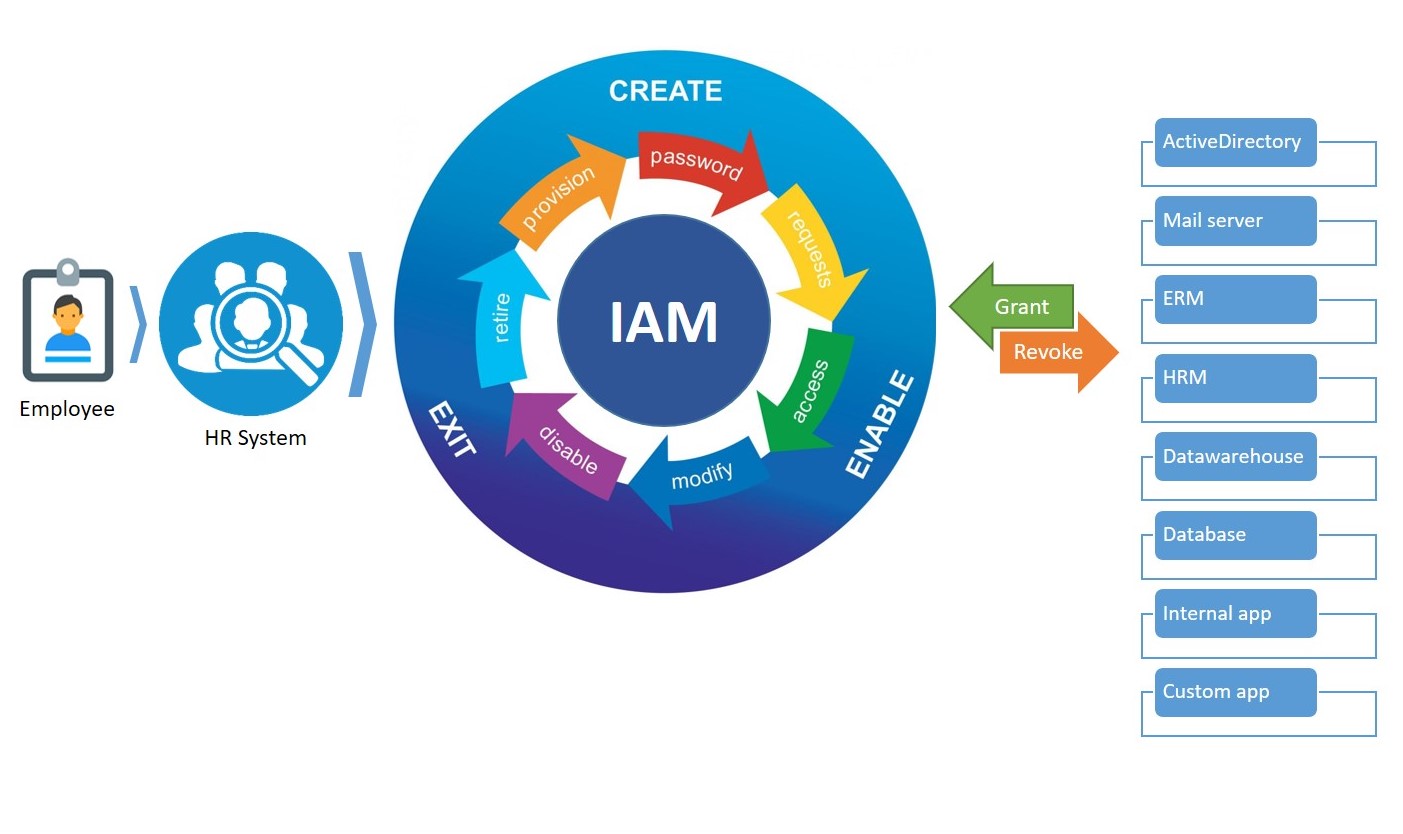
IAM solution allows enterprises to control fully the life cycle of an account of the system, from the beginning to the end of the user relationship.

With IAM, enterprises will have answers for questions:
- Who – The system has many roles, meaning of each role
- What – Each account is used for which application, for which purpose
- When – Valid time of each account
- Why – Reason for account grant, status change
- How – How to grant accounts, through which procedures and approvals