TOO MANY RISKS, TOO FEW SOLUTIONS. WHERE IS THE ANSWER?
Nowadays, organizations are facing a lot of difficulties in preventing the increasing threats to information security over time in both quantity and complexity. Risks such as ransomware, data theft, or internal data leakage, especially data related to business activities, can directly cause damages of up to hundreds of billions of VND or indirectly cause serious damage to the reputation of the organization.
However, the solutions to monitor and alert risks to information security from security vendors not only require a large investment in copyrights but also only provide efficiency when the enterprise has a team of experienced and skilled information security monitoring. Therefore, equipping solutions for monitoring and alerting information security risks while having a team to operate, monitor, and timely alert is always a balancing equation between "investment" and "effectiveness" - a difficult problem that organizations have to face. With HPT's Information Security Monitoring Service, organizations not only meet and balance the effectiveness - safety - cost but also keep up with the inevitable trend of investing in information security.
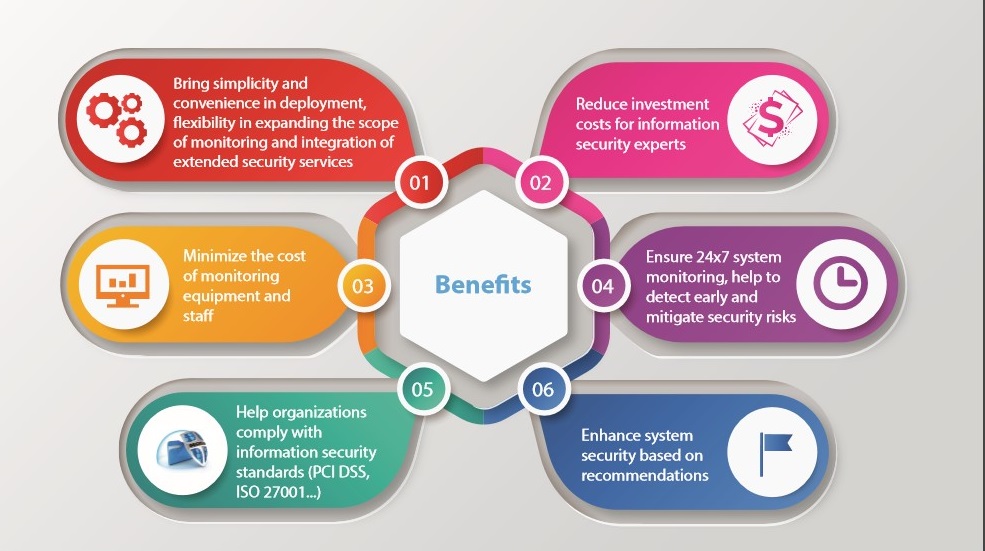
BENEFITS OF HPT MANAGED SERCURITY SERVICE (HMSS)
The use of Managed Security Services (MSS) is becoming an inevitable trend for businesses in the context of increasing cybersecurity threats and the limited effectiveness of self-defense measures. In comparison to the time, manpower, and resources needed for information security self-operation and monitoring, the advantages of adopting MSS are obvious.
ELEVATE THE SECURITY OF THE ORGANIZATION WITH THE INFORMATION SECURITY MONITORING SERVICE - ENSURING 24X7 INFORMATION SECURITY
The Information Security Monitoring Service is a comprehensive and 24x7 service that monitors the security of an organization's IT system, providing alerts on IT system risks and specific recommendations to enhance organizational security. This service enables the organization to proactively detect and mitigate potential risks to the system, thereby enhancing the level of security for the IT system
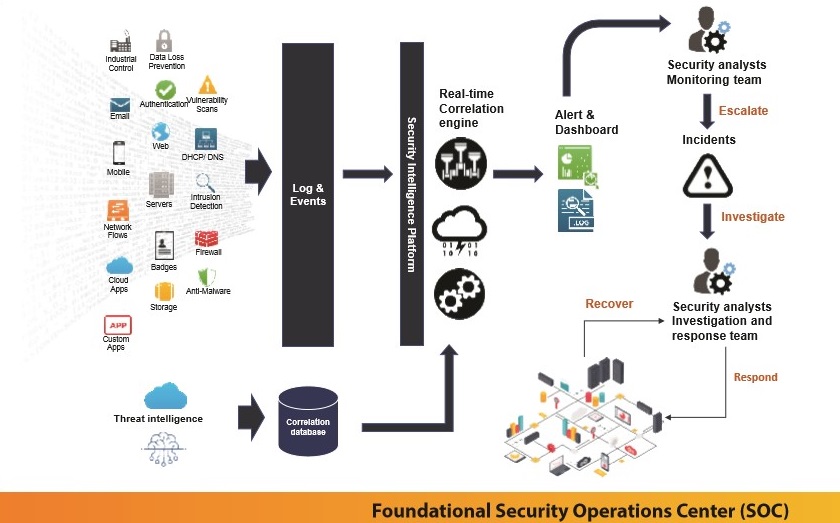
1. The monitoring component is placed within the customer's system with the task of collecting and processing data related to information security from servers, firewalls, applications, etc
2. The monitoring component will connect to HPT's centralized Information Security Operations Center (SOC) through a secure transmission channel
3. At the SOC, HPT's information security experts will continuously monitor events that could pose risks to the system 24x7, using automated tools combined with their professional expertise
4. The monitoring covers various types of information security risks and multiple stages of system attacks.
5. Alert customers when potential information security threats are detected
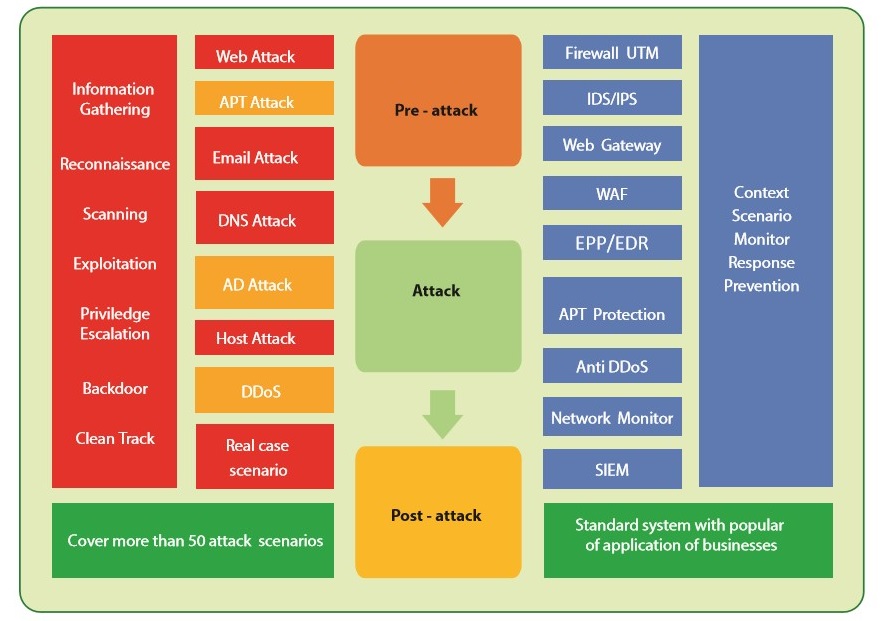
- Risks posed by different types of cyber-attacks, ranging from common to sophisticated, such as application attacks, system infrastructure attacks, and attacks on end-users
- The various stages of a Kill Chain attack, from information gathering and system scanning to the stages of the attack and aftermath.
- Other risks, such as system or software vulnerabilities.
6. Periodic report (weekly, monthly or quarterly) or emergency report on information security of customers' environment along with recommendations and instructions to protect and enhance information security.
STRENGTHS OF HPT INFORMATION SECURITY MONITORING SERVICE
HPT has nearly 30 years of experience consulting and providing in-depth information security services, deploying technology solutions from major security vendors for customers. Officially licensed by the Ministry of Information and Communications for the provision of Information Security services.
The organization's IT system is monitored and supervised by engineers with advanced professional certifications, extensive expertise, and monitoring technologies optimized to suit the characteristics of each organization's system. The Security expert team performs 24x7 monitoring, detection, analysis, alerting, and coordination to prevent information security threats at any time.
Providing enhanced information security services to assist businesses in maximizing their capacity to handle information security issues and risks:
The Security Assessment service identifies vulnerabilities and assesses the level of protection against potential security threats.
Threat Investigation and Threat Hunting services help to extensively scan the IT system, detect existing and deeply hidden threats.
The Incident Response service with experienced expert teams helps to recover the system when it is attacked, minimizing downtime and financial losses for the organization.
The Endpoint Detection & Response service detect and prevent malicious code on the endpoints in real-time from which to analyze and identify potential risks.